SolarWinds: The Most Sophisticated Supply Chain Attack in History
The Silent Intrusion: Beyond Traditional Hacking
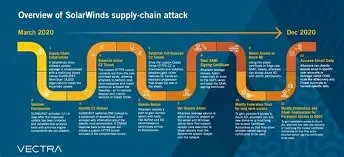
In late 2020, the world discovered SolarWinds Orion, a software used by thousands of organizations, had been turned into a Trojan horse. This wasn’t just a data breach; it was a "Supply Chain Attack." Kian Technologies analyzes this case to show how state-sponsored actors (APT29/Cozy Bear) bypassed the world’s best defenses by poisoning the source at its origin.
The Mechanism: The SUNBURST Backdoor
The attackers didn’t attack the customers directly. Instead, they compromised the Software Development Life Cycle (SDLC) of SolarWinds. They inserted a backdoor named SUNBURST into a legitimate Orion software update. When 18,000 customers—including the US Treasury, Pentagon, and Microsoft—installed this "trusted" update, they unwittingly invited the hackers into their networks.
- Stealth: The malware stayed dormant for two weeks to avoid detection by sandbox environments.
- Reconnaissance: It used DNS steganography to communicate with Command-and-Control (C2) servers without alerting firewalls.
- Lateral Movement: Once inside, hackers moved from the IT management server to the email systems (O365) and cloud environments.
Critical Failures and Industry Impact
Why did it take months to detect? The primary reason was Blind Trust. Organizations trusted the digital signature of the software update. Other failures included:
- Build Environment Security: SolarWinds’ internal build server was accessed using weak credentials (reportedly "solarwinds123").
- Lack of Egress Monitoring: Many organizations didn’t monitor where their servers were sending data "outbound."
Kian Technologies Expert Verdict: The Rise of SBOM
At Kian Technologies, we teach that Zero Trust means "Trust No Update." This case led to the mandatory use of SBOM (Software Bill of Materials). Our students learn to verify every component of a software package, ensuring that the software supply chain is transparent and secure. SolarWinds taught us that even your most trusted tools can be your biggest vulnerability.




0 Comments
No comments yet.