SolarWinds Supply Chain Attack Exposes Thousands of Organizations Worldwide
Published on: 08 Jul 2025
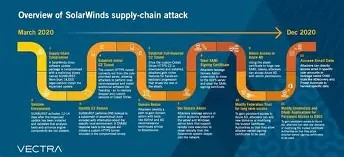
In late 2020, one of the most sophisticated cyberattacks in history was uncovered: the SolarWinds supply chain attack. Hackers, suspected to be a state-sponsored group dubbed APT29 or Cozy Bear, infiltrated the software development process of SolarWinds, a major IT management company. They inserted malicious code into a legitimate software update of the company’s Orion platform, which was then distributed to approximately 18,000 SolarWinds customers globally.
The attack was notable for its stealth, scale, and impact on government agencies, Fortune 500 companies, and critical infrastructure organizations.
🔍 How the Attack Worked
The attackers compromised SolarWinds’ build system and embedded a backdoor called Sunburst into the Orion software updates released between March and June 2020. When customers installed these updates, the malware created a covert communication channel allowing the hackers to:
Conduct reconnaissance on affected networks
Steal sensitive data including emails and intellectual property
Deploy additional malware for persistence and lateral movement
The supply chain nature of the attack meant that even highly secure organizations unwittingly installed compromised software, bypassing traditional perimeter defenses.
🕵️♂️ Scope and Impact
Victims of the SolarWinds breach included:
Multiple U.S. federal agencies including the Treasury, Commerce, and Homeland Security
Major technology firms like Microsoft, Cisco, and Intel
Energy and telecommunications companies
Numerous state and local governments
The breach compromised highly sensitive data and caused a significant intelligence setback for affected organizations, many of which only detected the intrusion months later.
❌ What Went Wrong
Key weaknesses that allowed the attack to succeed included:
Inadequate Build System Security
Attackers accessed SolarWinds’ software build environment, highlighting the need for stringent development controls.
Lack of Effective Software Supply Chain Validation
There were insufficient mechanisms to verify update integrity and provenance.
Slow Detection and Response
The attackers remained undetected for months, enabling extensive espionage.
Overreliance on Perimeter Defenses
Organizations trusted software updates without rigorous behavioral monitoring.
🔐 Lessons Learned
The SolarWinds breach transformed the cybersecurity landscape and forced a reevaluation of supply chain risks. Recommendations include:
Implement zero-trust architectures that verify all internal and external activity.
Adopt software bill of materials (SBOMs) to track components and dependencies.
Conduct continuous monitoring and anomaly detection to identify suspicious behavior.
Strengthen code signing and build environment protections.
Increase collaboration between vendors and customers to share threat intelligence.
🧠 Conclusion
The SolarWinds supply chain attack exposed the vulnerabilities inherent in modern software ecosystems and underscored the necessity of a holistic approach to cybersecurity that spans from development to deployment. Organizations must prioritize supply chain security and continuous vigilance to protect against increasingly sophisticated advanced persistent threats.
The attack was notable for its stealth, scale, and impact on government agencies, Fortune 500 companies, and critical infrastructure organizations.
🔍 How the Attack Worked
The attackers compromised SolarWinds’ build system and embedded a backdoor called Sunburst into the Orion software updates released between March and June 2020. When customers installed these updates, the malware created a covert communication channel allowing the hackers to:
Conduct reconnaissance on affected networks
Steal sensitive data including emails and intellectual property
Deploy additional malware for persistence and lateral movement
The supply chain nature of the attack meant that even highly secure organizations unwittingly installed compromised software, bypassing traditional perimeter defenses.
🕵️♂️ Scope and Impact
Victims of the SolarWinds breach included:
Multiple U.S. federal agencies including the Treasury, Commerce, and Homeland Security
Major technology firms like Microsoft, Cisco, and Intel
Energy and telecommunications companies
Numerous state and local governments
The breach compromised highly sensitive data and caused a significant intelligence setback for affected organizations, many of which only detected the intrusion months later.
❌ What Went Wrong
Key weaknesses that allowed the attack to succeed included:
Inadequate Build System Security
Attackers accessed SolarWinds’ software build environment, highlighting the need for stringent development controls.
Lack of Effective Software Supply Chain Validation
There were insufficient mechanisms to verify update integrity and provenance.
Slow Detection and Response
The attackers remained undetected for months, enabling extensive espionage.
Overreliance on Perimeter Defenses
Organizations trusted software updates without rigorous behavioral monitoring.
🔐 Lessons Learned
The SolarWinds breach transformed the cybersecurity landscape and forced a reevaluation of supply chain risks. Recommendations include:
Implement zero-trust architectures that verify all internal and external activity.
Adopt software bill of materials (SBOMs) to track components and dependencies.
Conduct continuous monitoring and anomaly detection to identify suspicious behavior.
Strengthen code signing and build environment protections.
Increase collaboration between vendors and customers to share threat intelligence.
🧠 Conclusion
The SolarWinds supply chain attack exposed the vulnerabilities inherent in modern software ecosystems and underscored the necessity of a holistic approach to cybersecurity that spans from development to deployment. Organizations must prioritize supply chain security and continuous vigilance to protect against increasingly sophisticated advanced persistent threats.