Microsoft Flags Multi-Stage AitM Phishing and BEC Attacks Targeting Energy Sector
The Strategic Shift in Business Email Compromise (BEC)
Microsoft Defender Security Research Team has issued an urgent warning regarding a highly sophisticated, multi-stage Adversary-in-the-Middle (AitM) and Business Email Compromise (BEC) campaign. This specific operation is laser-focused on the global Energy Sector, utilizing a combination of trusted infrastructures and psychological manipulation to bypass modern security perimeters.
Phase 1: Weaponizing SharePoint and the LOTS Strategy
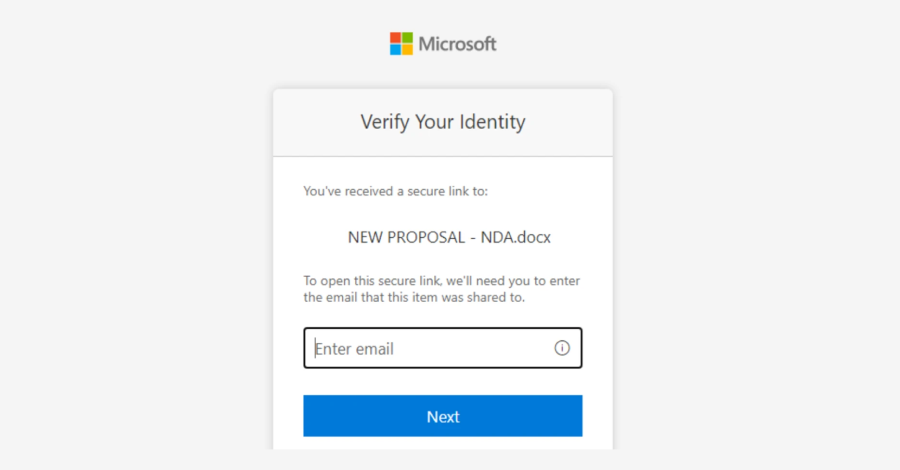
The attack begins with "Living-off-Trusted-Sites" (LOTS). Instead of hosting malicious payloads on suspicious domains, threat actors abuse legitimate SharePoint and OneDrive file-sharing services. By sending invitations from previously compromised trusted organizations, the phishing emails appear authentic to both automated email filters and the human eye.
- The Hook: A masqueraded SharePoint document-sharing workflow.
- The Bait: A URL that redirects users to a pixel-perfect fake credential prompt.
- The Catch: Because the session is proxied through the attacker’s infrastructure, they capture not just the password, but the Session Cookie, effectively bypassing standard Multi-Factor Authentication (MFA).
Phase 2: Post-Exploitation and Internal Propagation
Once the initial account is breached, the attacker doesn’t just steal data—they transform the inbox into a Phishing Hub. In one observed case, over 600 phishing emails were sent from a single compromised internal identity to contacts both within and outside the organization.
- Inbox Rule Manipulation: To remain undetected, attackers create hidden rules to move all incoming emails to the "Deleted Items" or "Archive" folder and mark them as read.
- Persistence: They even respond to suspicious recipients, reassuring them of the email’s authenticity before deleting the correspondence to hide the evidence.
- Lateral Movement: By leveraging the trusted identity of an energy firm executive or engineer, they cast a wider net to compromise partners and supply chain vendors.
The "rn" vs "m" Deception: Homoglyph Attacks
Beyond AitM, researchers have noted a rise in Homoglyph attacks. Attackers use visual similarities to deceive victims. A common trick is replacing the letter "m" with "rn" (e.g., rnicrosoft.com instead of microsoft.com). This is particularly dangerous in internal corporate terms like "confirmation," "communication," or "member," where the human brain "auto-corrects" the visual discrepancy.
Advanced Vishing Kits and Real-Time Authentication Control
Adding to the complexity, Okta has detected custom phishing kits designed for Voice Phishing (Vishing). These kits allow a live attacker on a phone call to synchronize the victim’s browser with their verbal instructions in real-time. This "synchronization" allows attackers to guide users through approving push notifications or entering OTPs, defeating non-phishing-resistant MFA methods.
Kian Technologies Expert Recommendations
Microsoft emphasizes that a Password Reset is insufficient for an AitM attack. At Kian Technologies, we recommend the following defense-in-depth strategy:
- Revoke Session Cookies: In the event of a breach, all active sessions must be forcefully revoked via the Identity Provider (IdP).
- Phishing-Resistant MFA: Move toward hardware-based keys (FIDO2/YubiKeys) or Certificate-Based Authentication.
- Conditional Access: Implement policies that restrict access based on location, device health, and impossible travel telemetry.
- Continuous Access Evaluation (CAE): Enable real-time session monitoring to terminate access the moment a risk is detected.
Conclusion
The energy sector is a high-value target for both cybercriminals and state-sponsored actors. As attackers move away from building their own infrastructure to abusing trusted platforms like AWS, Google Drive, and SharePoint, the burden of security shifts toward Identity Governance. Vigilance and advanced MFA are no longer optional—they are the final line of defense.





6 Comments
Rahul Verma (24 Jan 2026, 04:00 PM)
The BEC campaign targeting the energy sector is alarming. Good catch!
Priya Patel (24 Jan 2026, 11:00 AM)
Quality post as always! Keep up the good work, Kian Technologies.
Vikram Singh (24 Jan 2026, 10:00 AM)
The BEC campaign targeting the energy sector is alarming. Good catch!
Tanuja Mishra (24 Jan 2026, 09:00 AM)
Very insightful post! This really helps in understanding modern threats.
Sanjay Bose (24 Jan 2026, 12:00 AM)
Another great post. Looking forward to more deep dives like this.
Amit Mehra (23 Jan 2026, 09:00 PM)
Clear, professional, and technical. Exactly what a security blog should be.