Microsoft: Russian-Linked Hackers Using 'Device Code Phishing' to Hijack Accounts
The Rise of Device Code Phishing
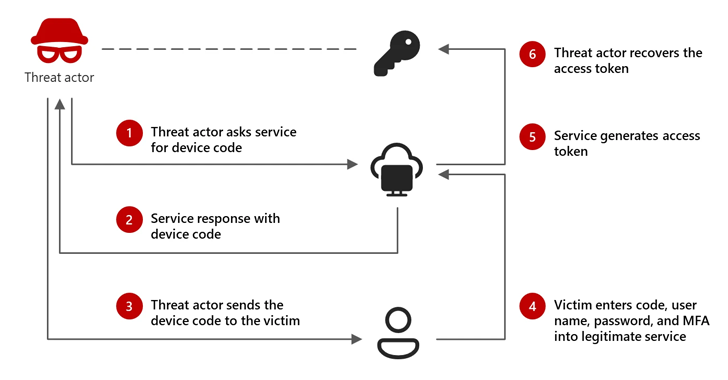
Microsoft Threat Intelligence has issued a warning regarding a new Russian-aligned threat actor, Storm-2372. Since August 2024, this group has been targeting critical sectors globally—including government, defense, and telecommunications—using a highly effective technique known as Device Code Phishing.
How the Attack Works
Unlike traditional phishing that steals passwords, this method tricks users into authorized access without ever needing a password:
- The Hook: Attackers send fake Microsoft Teams invites or messages via WhatsApp/Signal.
- The Trick: They generate a legitimate device code and ask the victim to enter it into a real Microsoft sign-in page.
- The Theft: Once the code is entered, the attacker captures the Authentication Tokens, giving them full access to the victim's account and data.
Persistence and Lateral Movement
Once inside, Storm-2372 uses the Microsoft Graph service to search for keywords like "password," "admin," and "secret." They then move laterally within the organization by sending phishing messages from the compromised account to other employees. Recent updates show they are now even registering their own devices within Entra ID to maintain long-term access.
How to Protect Your Organization
Microsoft recommends blocking device code flows where not required and enforcing phishing-resistant MFA (like FIDO2 keys). Following the principle of least privilege is also crucial to limit the damage if an account is breached.
Master Advanced Phishing Defense
As hackers find new ways to bypass MFA, the world needs experts who can secure enterprise environments. Learn the latest defense strategies at the Best Ethical Hacking Institute in Bhilai & Raipur. Join our Cybersecurity program today!






4 Comments
Aravind Sharma (15 Feb 2025, 08:08 PM)
Interesting read on the Osiris ransomware. The POORTRY driver is a serious threat.
Priya Patel (15 Feb 2025, 05:08 PM)
Interesting read on the Osiris ransomware. The POORTRY driver is a serious threat.
Kiran Deshmukh (15 Feb 2025, 04:08 PM)
Interesting read on the Osiris ransomware. The POORTRY driver is a serious threat.
Suresh Iyer (15 Feb 2025, 10:08 AM)
Great analysis by Kian Technologies. Keeping our systems patched is indeed critical.