Surge in Software Supply‑Chain Attacks Hits IT, Telecom, and Beyond
By: Kian |
July 08, 2025 10:03 AM IST |
1 min read
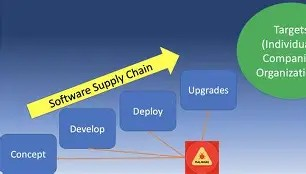
The Supply-Chain Crisis
Between April and May 2025, software supply-chain incidents skyrocketed by 90% year-over-year. Attackers are no longer just targeting companies directly; they are infecting the software and vendors those companies trust. This "deep reach" allows a single compromise to impact thousands of downstream clients.
Key Highlights
- IT & Telecom: 63% of the victims were service providers.
- Crypto24 & Killsec: These groups have stolen terabytes of data by breaching vendor credentials.
- Stealth: Malicious code signed with valid certificates makes detection nearly impossible for standard scans.
Mitigation: The Role of SBOM
Organizations must maintain a Software Bill of Materials (SBOM) and isolate their CI/CD pipelines to prevent cross-contamination from third-party libraries.
Become a Cybersecurity Analyst
Learn how to audit vendor risks and secure supply chains. Join the Best Ethical Hacking Institute in Chhattisgarh. Visit Kian Technologies today!
Become a Malware Analysis Expert As hackers switch to modern languages like Golang to build evasive tools, the industry needs experts who can deconstruct and stop these threats.
Join the Best Ethical Hacking Institute in Bhilai & Raipur: Learn Malware Analysis, Reverse Engineering, and Advanced Threat Hunting. Enroll now to start your journey in Cybersecurity!





3 Comments
Rohan Joshi (09 Jul 2025, 12:03 AM)
Practical mitigations mentioned here are very useful for small businesses.
Aravind Sharma (08 Jul 2025, 06:03 PM)
The point about homoglyph attacks (rn vs m) is something everyone should watch out for.
Anjali Gupta (08 Jul 2025, 10:03 AM)
Solid advice on MFA. Most organizations still underestimate its importance.