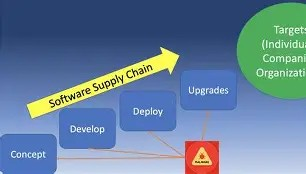
Surge in Software Supply‑Chain Attacks Hits IT, Telecom, and Beyond
08 Jul 2025
Between April and May 2025, Cyble Intelligence reported a sharp increase in software supply‑chain incidents—from ~13 per month to nearly 25 monthly events
thetimes.co.uk
+15
thecyberexpress.com
+15
cybersecurityhq.com
+15
reddit.com
. This represents a 90% jump year-over-year, highlighting attackers’ growing focus on exploiting trusted vendor ecosystems.
Distribution by Industry:
63% of impacted organizations were IT, software, and telecom service providers.
Other sectors—finance, Healthcare, Manufacturing—also significantly targeted.
Example Threats Identified:
Crypto24 claimed 3 TB of stolen data from a Singapore IT firm.
Killsec breached Australian telecom vendor, stealing app configs and credentials
cyble.com
.
Why Supply-Chain Breaches are Dangerous:
Deep reach: A single compromise can impact thousands of downstream clients.
Trust abused: Software signed with valid certificates makes detection difficult.
Harder detection: Legitimate code used maliciously can evade standard scans.
Mitigation Measures:
Perform SBOMs: Maintain software inventory with provenance metadata.
Isolate build environments: Separate CI/CD pipelines per project/vendor.
Validate third-party libs: Errata studies and integrity verification should be standard.
Monitor vendor relationships: Vet security policies before integration or maintenance.
Incident tabletop exercises: Simulate supply chain compromise scenarios.
Takeaway:
As dependency complexity grows, the attack surface widens. April–May 2025 highlighted that existing tools and awareness aren’t enough; organizations must proactively harden build pipelines, vet vendors, and adopt zero-trust architectures around supply dependencies.
thetimes.co.uk
+15
thecyberexpress.com
+15
cybersecurityhq.com
+15
reddit.com
. This represents a 90% jump year-over-year, highlighting attackers’ growing focus on exploiting trusted vendor ecosystems.
Distribution by Industry:
63% of impacted organizations were IT, software, and telecom service providers.
Other sectors—finance, Healthcare, Manufacturing—also significantly targeted.
Example Threats Identified:
Crypto24 claimed 3 TB of stolen data from a Singapore IT firm.
Killsec breached Australian telecom vendor, stealing app configs and credentials
cyble.com
.
Why Supply-Chain Breaches are Dangerous:
Deep reach: A single compromise can impact thousands of downstream clients.
Trust abused: Software signed with valid certificates makes detection difficult.
Harder detection: Legitimate code used maliciously can evade standard scans.
Mitigation Measures:
Perform SBOMs: Maintain software inventory with provenance metadata.
Isolate build environments: Separate CI/CD pipelines per project/vendor.
Validate third-party libs: Errata studies and integrity verification should be standard.
Monitor vendor relationships: Vet security policies before integration or maintenance.
Incident tabletop exercises: Simulate supply chain compromise scenarios.
Takeaway:
As dependency complexity grows, the attack surface widens. April–May 2025 highlighted that existing tools and awareness aren’t enough; organizations must proactively harden build pipelines, vet vendors, and adopt zero-trust architectures around supply dependencies.